1. Introduction
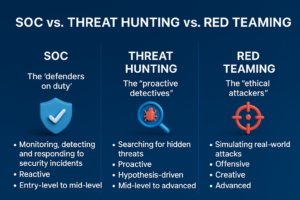
In an era where cyberattacks make headlines daily from massive data breaches at corporations to state-sponsored espionage the demand for cybersecurity professionals has skyrocketed. But not all roles are created equal. While traditional security jobs focus on reactive measures like patching vulnerabilities after an incident, there’s a surging interest in proactive roles that anticipate and outmaneuver threats. These positions empower experts to stay one step ahead of adversaries, turning defense into an active pursuit. Enter the Security Operations Center (SOC), threat hunting, and red teaming—three interconnected yet distinct paths in cybersecurity.
SOC analysts monitor and respond to threats in real-time, threat hunters proactively seek out hidden dangers, and red teamers simulate attacks to expose weaknesses. Though they overlap in tools and goals, each requires a unique mindset and skill set. This article will break them down side by side, highlighting pros, cons, and synergies to help you decide which aligns with your strengths and career aspirations. Whether you’re a beginner eyeing entry-level roles or an intermediate pro considering a pivot, we’ll guide you through self-assessment and practical steps.
2. Background: The Cybersecurity Landscape
Cybersecurity has evolved dramatically from its early days of basic firewalls and antivirus software. The shift from reactive to proactive security stems from the realization that waiting for alerts isn’t enough; sophisticated threats like advanced persistent threats (APTs) can lurk undetected for months. Today, organizations adopt a layered approach: operations for day-to-day monitoring, detection for uncovering stealthy intrusions, and offense for testing defenses.
In a typical security organization, roles fall into blue team (defensive), red team (offensive), and purple team (collaborative) categories. SOCs form the backbone of blue team operations, handling continuous vigilance. Threat hunting bridges blue and purple by actively searching for anomalies beyond automated alerts. Red teaming embodies the red side, mimicking real-world attackers to improve overall resilience. Together, they create a robust ecosystem where insights from one role enhance the others, adapting to the ever-changing threat landscape.
3. What is SOC? (Security Operations Center)
A Security Operations Center (SOC) is a centralized unit that monitors, detects, and responds to cybersecurity incidents in real-time. Its core purpose is to maintain an organization’s security posture by identifying and mitigating threats before they escalate. SOCs operate 24/7, acting as the first line of defense.
Typical functions and responsibilities include:
- Monitoring and Alerting: Continuously scanning networks, endpoints, and logs for suspicious activity using tools like SIEM (Security Information and Event Management) systems.
- Incident Triage and Response: Prioritizing alerts, investigating potential breaches, and coordinating remediation efforts.
- Log Management and Threat Intelligence: Aggregating data from various sources and integrating external threat feeds to enhance detection accuracy.
- Reporting and Compliance: Generating reports on incidents and ensuring adherence to regulatory standards like GDPR or HIPAA.
Key skills needed encompass analytical thinking, knowledge of networking protocols, and proficiency in tools such as Splunk, ELK Stack, or Microsoft Sentinel. Entry-level roles often require certifications like CompTIA Security+.
Pros of working in a SOC:
- Stable career path with high demand and job security.
- Opportunities for shift work, allowing work-life balance in some setups.
- Exposure to a wide range of threats, building broad expertise.
Challenges:
- High-stress environment with alert fatigue from false positives.
- Repetitive tasks, especially in Tier 1 roles, leading to burnout.
- Requires constant vigilance, often involving odd hours.
Resource:
What is SOC (Security Operations Center)? | InfosecTrain Explains It All
4. What is Threat Hunting?
Threat hunting is the proactive process of searching for malicious actors or activities within an organization’s environment that have evaded traditional detection methods. Unlike SOC’s reactive monitoring, threat hunting assumes breaches have occurred and focuses on finding them before significant damage. It’s hypothesis-driven, blending detective work with data analysis.
The methodology typically follows these steps:
- Hypothesis Development: Formulating educated guesses based on threat intelligence (e.g., “An insider might be exfiltrating data via unusual ports”).
- Data Gathering: Collecting logs, network traffic, and endpoint data from sources like EDR (Endpoint Detection and Response) tools.
- Analysis: Using techniques such as anomaly detection, behavioral analytics, or machine learning to uncover patterns.
- Remediation: Documenting findings and recommending actions to neutralize threats.
Threat hunters target advanced threats like long-dwell malware, insider risks, or zero-day exploits. Tools include Volatility for memory forensics, Zeek for network analysis, and platforms like Splunk or Elastic.
Required skills include deep forensics knowledge, scripting (Python/Bash), and a curious, investigative mindset. Certifications like GIAC Certified Threat Hunter (GCTH) are beneficial.
Pros:
- Intellectually stimulating, with autonomy in investigations.
- Direct impact on reducing breach dwell time.
- Opportunities for creative problem-solving.
Challenges:
- Resource-intensive, requiring access to vast data sets.
- Potential for “hunting fatigue” if hypotheses yield few results.
- Demands advanced skills, making entry harder without prior experience.
Resource:
What Is Threat Hunting and How to Get Started
5. What is Red Teaming?
Red teaming involves simulating real-world cyberattacks to evaluate an organization’s defenses, detection capabilities, and response procedures. The goal is to think like an adversary, identifying vulnerabilities that could be exploited by malicious actors. It’s offensive security at its core, often conducted periodically rather than continuously.
Common techniques include social engineering (phishing simulations), lateral movement within networks, and stealthy persistence methods. Phases of an engagement:
- Reconnaissance: Gathering intel on targets via OSINT (Open-Source Intelligence).
- Initial Intrusion: Exploiting weaknesses like weak passwords or unpatched software.
- Lateral Movement and Persistence: Spreading across systems while evading detection.
- Exfiltration and Reporting: Simulating data theft, then debriefing with recommendations.
Skills involve ethical hacking, tools like Metasploit, Burp Suite, or Cobalt Strike, and knowledge of TTPs (Tactics, Techniques, and Procedures) from frameworks like MITRE ATT&CK. Certifications such as OSCP (Offensive Security Certified Professional) are highly valued.
Pros:
- Exciting, “hacker-like” work with variety in engagements.
- High earning potential and prestige.
- Contributes to real improvements in security postures.
Challenges:
- Ethical boundaries and legal risks if scopes aren’t clear.
- Physically and mentally demanding, with irregular project-based work.
- Requires constant upskilling due to evolving threats.
Resource:
RED TEAMING explained in 8 Minutes
6. Comparing the Three: SOC vs Threat Hunting vs Red Teaming
To highlight distinctions, here’s a comparison table:
| Aspect | SOC | Threat Hunting | Red Timing |
| Objective & Focus | Reactive defense: Monitor and respond to alerts. | Proactive detection: Seek hidden threats. | Offensive simulation: Test and expose weaknesses. |
| Time Horizon | Continuous, 24/7 operations. | Ongoing but hypothesis-based hunts. | Periodic engagements (e.g., quarterly). |
| Mindset & Style | Vigilant, process-oriented; team collaboration. | Investigative, curious; independent analysis. | Adversarial, creative; strategic planning. |
| Team Interactions | Works with IT, compliance; feeds into hunting. | Collaborates with SOC for data; informs red teams. | Purple teaming with blue teams for debriefs. |
| Overlaps | Shares tools like SIEM; basic hunting in advanced SOCs. | Builds on SOC alerts; uses red team TTPs for hypotheses. | Insights improve SOC rules and hunting methods. |
| When Needed | Essential for all orgs; baseline security. | Mature orgs with data richness. | High-risk sectors like finance or government. |
7. Which Path Might Be Right for You? (How to Decide)
Choosing between SOC, threat hunting, and red teaming starts with self-assessment. Consider your strengths: If you thrive in structured environments and enjoy teamwork, SOC might suit you. For those with a detective’s instinct and patience for deep dives, threat hunting calls. If creativity and ethical hacking excite you, red teaming could be ideal.
Beneficial transitions often follow SOC → Threat Hunting → Red Teaming, building defensive knowledge before offensive skills. In small orgs, SOC roles dominate due to limited resources, while large enterprises support specialized hunting and red teams.
Certifications and advice:
- SOC: Security+, CySA+; start with entry-level analyst roles.
- Threat Hunting: GCTH, CHFI; gain experience via SOC or IR teams.
- Red Teaming: OSCP, CREST; practice on platforms like Hack The Box.
Sample roadmap: Begin as a SOC Tier 1 (1-2 years), advance to threat hunter (3-5 years), then red team operator (5+ years).
8. Integrating & Collaborating: Why All Three Matter
Cybersecurity isn’t siloed; success demands integration. SOC provides the foundation, but without hunting, subtle threats slip through. Red teaming reveals gaps that hunting can then monitor, creating a feedback loop. The purple team approach—collaborating blue and red—ensures exercises like tabletop simulations strengthen all areas.
Best practices include regular knowledge sharing, joint training, and using shared platforms like MITRE ATT&CK for alignment. Ultimately, these roles complement each other, fostering a resilient security culture.
9. Case Studies / Example Scenarios
In a small startup, initial reliance on a basic SOC evolved after a phishing incident. They added threat hunting by training analysts to probe logs proactively, reducing incident response time by 40%.
A mature bank employed red teaming to simulate an APT attack, uncovering unmonitored lateral movement. Post-engagement, threat hunters incorporated those TTPs into routine scans, while SOC updated rules—preventing a real breach months later.
Personal profile: Jane Doe started in SOC, honing monitoring skills. She transitioned to threat hunting after certifications, then joined a red team, crediting the progression for her comprehensive expertise.
10. Conclusion
SOC offers steady defense, threat hunting proactive discovery, and red teaming offensive insights—each with unique pros like stability, intellectual challenge, and excitement, but cons such as stress or skill demands. Weigh trade-offs against your interests: stability vs. adventure.
Experiment hands-on with CTFs on TryHackMe or build a home lab. Pick what excites you, but remain open to cross-role shifts for growth.
11. Further Resources
- Books: “The Threat Hunter’s Handbook” by Chris Sanders,”Red Team Field Manual” by Ben Clark.
- Blogs/Training: TechSkillSchool Academy courses; Black Hills Infosec blog; Offensive Security for red team training.
- Tools/Platforms: Splunk (free tier), Wireshark, Hack The Box.
- Communities: Reddit’s r/netsec, r/ThreatHunting; DEFCON forums; GIAC certifications hub.